Security
pdd (Palm dd)
pdd (Palm dd) is a Windows-based tool for memory imaging and forensic acquisition of data from the Palm OS family of PDAs. pdd will preserve the crime scene by obtaining a bit-for-bit image or “snapshot” of the Palm device’s memory contents. Such data can be used by forensic investigators, incident response teams, and criminal and civil prosecutors. [ continue ]
Decoding the Mobitex Protocol
This paper examines the Research In Motion RIM 950 and RIM 957 BlackBerry Wireless Handhelds and details the process and tools required to capture data transmissions, decode the wireless Mobitex protocol, and retrieve all e-mail and associated attachments that are sent from Internet Edition devices. [ continue ]
Authentication Tokens: Balancing the Security Risks with Business Requirements
Stolen passwords represent a significant threat to today’s enterprise. It has become apparent that a simple username and static password combination to login to a system is not adequate to protect most business information. As the corporate network is increasingly used to store disparate levels of company confidential information, there is a need for user access control. Authentication tokens are hardware or software devices that generate dynamic one-time passwords through the use of a mathematical function. This report examines the business needs, deployment strategies, and security risk scenarios of hardware vs. software-based token technologies. No single technology will provide the ultimate solution for every situation, and there are advantages and disadvantages to the use of each type. [ continue ]
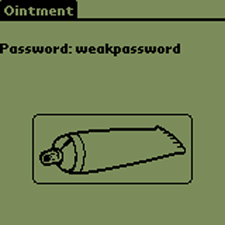
Ointment
Ointment exploits a design problem with the Palm OS Debug Mode and the use of weak obfuscated system passwords. Ointment will emulate the Palm OS serial link protocol (SLP) and the ‘export’ and ‘reset’ commands of the Palm OS Console Debug Mode, retrieve the encoded password block from the “Unsaved Preferences” database of the target device, and decode and display the resultant ASCII password. [ continue ]
Security Analysis of the Palm Operating System
Portable devices, such as Personal Digital Assistants (PDAs), are particularly vulnerable to malicious code threats due to their widespread implementation and current lack of a security framework. The presented research provides detail into specific scenarios, weaknesses, and mitigation recommendations related to data protection, malicious code, virus storage, and virus propagation. [ continue ]