Security
Wardialing Brief
Wardialing consists of using a computer to dial a given set of telephone numbers with a modem. Each phone number that answers with modem handshake tones and is successfully connected to is stored in a log. By searching a range of phone numbers for computers, one can find entry points into unprotected systems and backdoors into seemingly secure systems. This brief paper introduces the concept of wardialing, examines concerns with today’s network setups, and contains a reference of related news reports, security papers, software tools, and Internet resources. [ continue ]
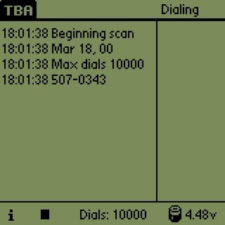
TBA: The Palm OS Wardialer
TBA (previously known as BootyCall) is the first wardialer for the Palm OS platform. No more using a desktop or laptop for scanning. Using a Palm device with a modem, you can wardial from anywhere a phone line is available – throw it in a telephone can to retrieve later, toss it up in the ceiling during a security audit – the possibilities are endless. TBA is fully featured, free, and unsupported. [ continue ]
Introduction to the iButton
This paper introduces and gives an overview to the Dallas Semiconductor (now Maxim Integrated Products) iButton family, focusing on the hardware component, and examines potential areas that may be susceptible to attack. These areas may yield vulnerabilities or problems related to the security of the device. Detail is placed on the Java-powered cryptographic iButton, which plays a major role in the implementation of PKI (Public Key Infrastructure) or other solutions where security, authentication, and/or encryption is needed. Simple software routines to communicate with the iButton are also presented. [ continue ]
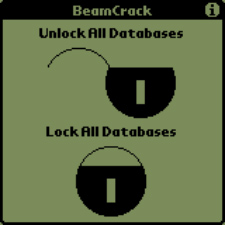
BeamCrack
BeamCrack will allow or prevent a Palm OS application from being “beamed” (via infrared) to another Palm device by changing a single bit in each application’s database header. [ continue ]
MAC Address Cloning
At one time or another, you may find it necessary to have two network interface cards (NICs) with the same physical network, or Media Access Control (MAC), address. This could be for a number of reasons including the testing of your internal network, software experimentation, or bypassing software protection mechanisms. This paper examines the design of typical NICs and the process used to change the MAC address stored in non-volatile memory on the card. [ continue ]